In every AWS account, a default VPC is automatically created in every region. This default VPC makes experimentation and initial tasks easy. But beware because the default VPC has very permissive security settings. By default, public access to and from the Internet is not blocked by the network ACLs associated with the default VPC, all subnets are public, and instances get public IPs by default. Ideally, you should create a new custom VPC and configure it in a secure manner. When you create a new VPC, it is isolated by default. This means that no other VPCs have access to the new VPC. There is no public access to or from the Internet unless it is configured.
A security group is a stateful firewall that is applied to individual interfaces on various network-based resources, including EC2 and RDS instances running in a VPC. It can also be applied to interfaces that are used by Lambda functions. A new security group allows all traffic outbound by default. There are no statements regarding inbound traffic. The security group ends in an implicit deny all, meaning that any traffic that is not explicitly allowed will be denied.
Therefore, by default, a new security group allows all outbound traffic and no inbound traffic. However, the security group is stateful and will allow inbound traffic that is a response to an existing connection. In Figure 11.8, you can see the default ruleset for a new security group.
When a security group is assigned to an EC2 instance, it is applied to the first interface by default. When an instance has multiple interfaces, different security groups can be applied to each interface.
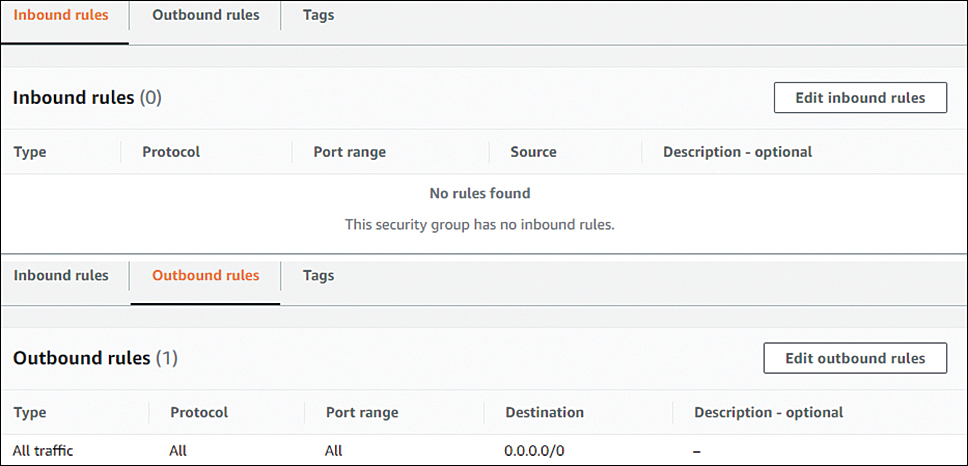
FIGURE 11.8 Default rules for a new security group
A network access control list is a stateless firewall that is applied to a subnet. Because an NACL is stateless, when a new NACL is created, rules must be configured in both directions to permit traffic to flow. Every subnet must be associated with an NACL. All inbound and outbound traffic is denied by default when a new NACL is created. NACL rules are applied in order from the top down. In Figure 11.9, you can see the default ruleset for a new NACL.
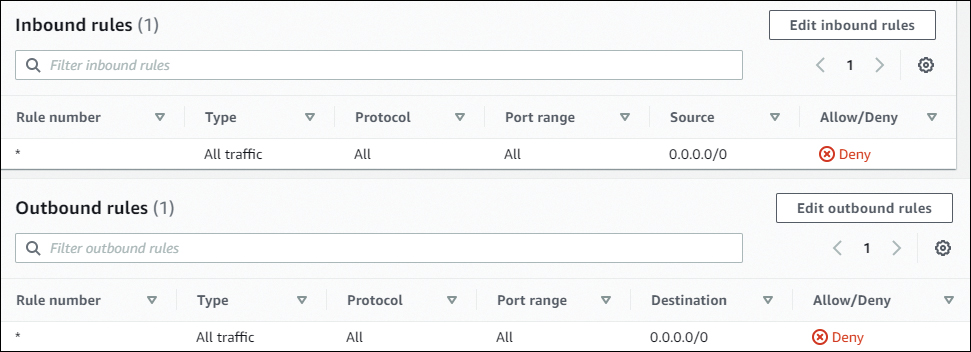
FIGURE 11.9 Default rules for a new network access control list
Public subnets are associated with a route table that has a default route pointed to an Internet gateway. Instances in a public subnet are usually configured with public IP addresses (though not required). Private subnets are not configured with a route to the Internet gateway and require a Network Address Translation (NAT) gateway or NAT instance to access the Internet.
VPC Flow Logs are an important tool for VPC security. VPC flow logs can be used to monitor the network traffic in your Amazon VPC. You will learn more about flow logs in Chapter 13, “Troubleshoot Network Connectivity.”
You must be able to differentiate between security groups and NACLs and their use cases. Security groups are stateful and applied to individual interfaces. NACLs are stateless and are applied to entire subnets.