The AWS virtual private gateway is a virtual VPN endpoint that terminates a site-to-site VPN connection that attaches to a single VPC. A maximum of 10 external VPN tunnels that are not VPC networking locations per virtual private gateway are supported, and each of the tunnels connects using the IPSec protocol.
A virtual private gateway (VGW) is the VPN endpoint connector on the AWS side of the site-to-site VPN connection, as shown in Figure 6.22. This is an AWS managed logical gateway endpoint used to create the IPSec VPN tunnel from the AWS VPC to an on-premises customer gateway at the customer end of the connection. The maximum throughput through the gateway is 1.25 Gbps. However, that actual throughput is dependent on such factors as packet size, if the protocol is TCP or UDP, latency in the network, and the capacity of the connection. The maximum packets per second through the gateway is 140,000. The maximum number of BGP advertised routes is 1,000 dynamics and 100 statics.
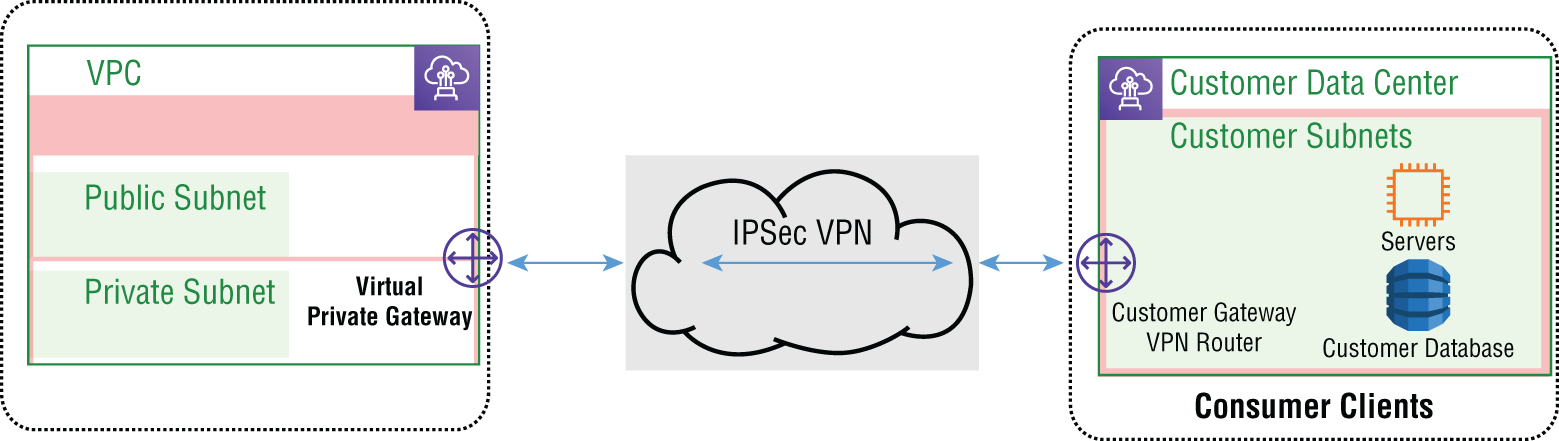
FIGURE 6.22 Virtual private gateway
The VPN tunnel is established after traffic is generated from the customer side of the VPN connection.
Site-to-site VPNs are created using encrypted tunnels over the Internet from your on-premises network to a VPC in an AWS region using the IPSec protocol suite to encrypt the in-flight traffic, as shown in Figure 6.23. In contrast to Direct Connect where it can take weeks or months to activate connectivity, a VPN can be created in less than an hour by using your existing Internet connections. The VPN can be used as the primary interconnection between your on-premises data center and AWS. VPNs can also be used to back up a Direct Connect link should it fail. Also, the site-to-site VPNs can traverse over the DX to provide an encrypted tunnel over the Direct Connect link.
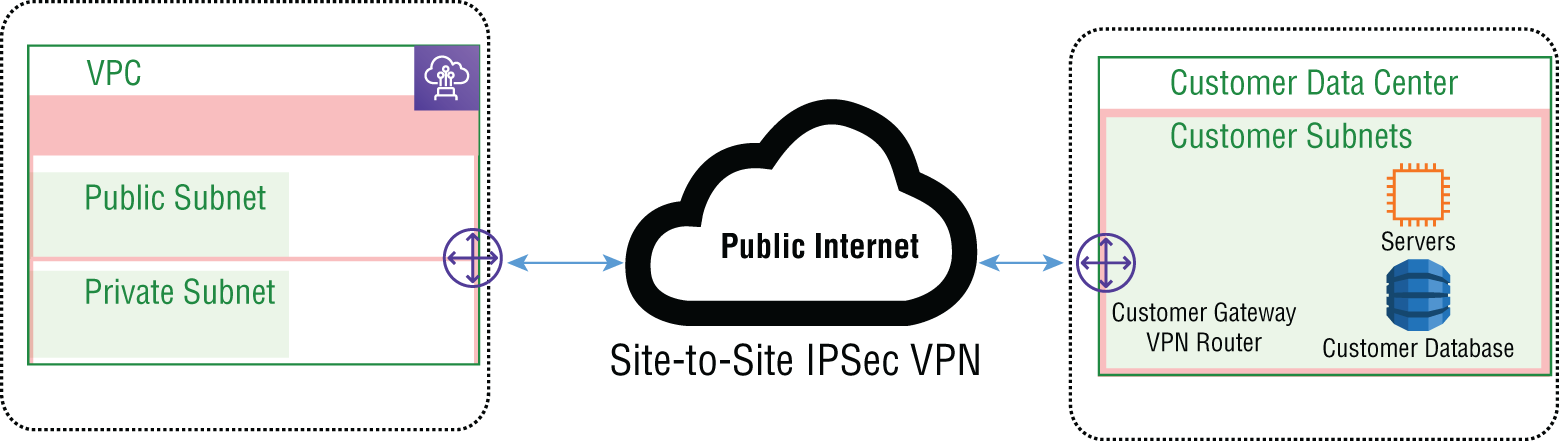
The AWS site-to-site VPN is a managed IPSec VPN service from an AWS VPC to your corporate data center. Major components of an AWS site-to-site VPN include the VGW and the VPN router interface that resides in a AWS region at the VPC level that terminates the connection from your on-premise Customer Gateway (CGW), which is usually a physical router that the VPN connects to. The VPN connection is between the VGW and the CGW. The customer router is a physical device running VPN software.
Setting up a site-to-site VPN depends on how you are implementing the VPN; it can be either through Direct Connect or over the public Internet. You must record the IP address of the CGW router’s outside-facing interface that is reachable from AWS over either Direct Connect or the Internet. You will also need to provide AWS with the subnets at your location that they will route to. The VPG is a highly available VPN router virtual machine that is created in your account and associated with a VPC that you want your remote site to connect to. The VGW has two outside interfaces that are connected as endpoint 1 and endpoint 2, and these interfaces have publicly reachable IPv4 addresses. This provides a high-availability VPN design into AWS as each endpoint resides in a different availability zone. Note that if you have only one VPN router at your location, the connection will not be highly available as it will be a single point of failure. For full high availability, two separate VPN routers at the on-premises location and separate Internet or DX connections would be required.
In AWS there are two routing options for the VPN connections, static and dynamic. The static VPN uses hard-coded, static routing to advertise the routes or dynamic routing using the BGP as the routing protocol, which requires BGP support on your customer router. Static does not use any dynamic routing protocols and requires that you hard-code the static routes into the routing table. Static routing is useful over a single connection; however, with multiple paths between on-premise and AWS where failover or path load balancing is desired, BGP must be used for its ability to dynamically update the routing tables as the network conditions change. Inside the VPC, routes can automatically be updated based on the BGP route table by enabling route propagation. Later in this chapter we will cover static routing and BGP basic operations.
As we learned earlier, there is a maximum speed per VPG at the AWS location of 1.25 Gbps and a maximum of 140,000 packets per second (PPS) per VPN tunnel. This does not take into account the throughput capabilities of your on-site router and the speed of the Internet connection. The VGW speed limitation is the maximum speed regardless of how many VPN connections are configured. The total throughput will always be a maximum of 1.25 Gbps. Latency over the Internet will be inconsistent and based on the number of router hops, congestion, and distance. Internet latency can vary and cannot be controlled by the customer accessing the Internet.
The AWS VPN service is charged per hour, and AWS data transfer charges for all data transferred via the VPN connection are applied. Pricing varies per region and can be determined on the AWS web console.