The AWS network load balancer (NLB) is used for very high-performance use cases and operates at the network layer, layer 4, of the OSI model. The service has a lengthy list of features, as illustrated in Figure 1.15. The NLB can handle millions of connections per second and is used in very demanding and large implementations that benefit from high-throughput, low-latency connections. It supports large connection bursts and highly variable traffic patterns and uses a single IP address per availability zone. Targets can include EC2 instances, microservices, Lambda, and containers such as ECS and EKS. Both TCP and UDP IP connections are supported.
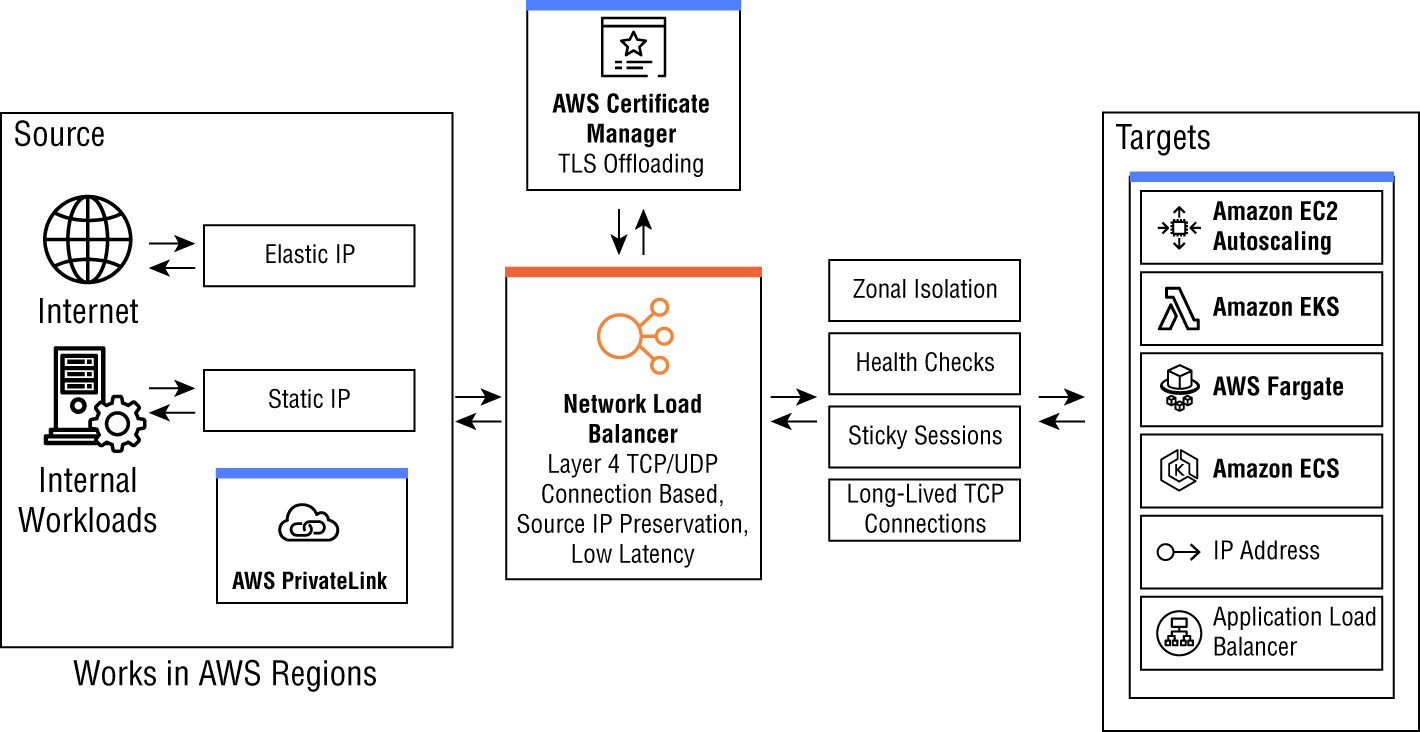
When an NLB is created in an availability zone, the ELB node gets created in that AZ to service local nodes that are only in that AZ. Cross-zone load balancing is also supported, and the NLB, when configured in this mode, will also load balance targets in other availability zones external to where it is configured. By configuring multiple availability zone targets in a target group, high availability is achieved and will continue to operate even if the AZ goes offline by utilizing DNS to route traffic to load balancers in other zones. Targets can be added or removed during production operations. The service can scale up or down by adding and removing targets dynamically to meet load requirements.
High performance is achieved by using a hash for each connection that is based on the TCP protocol, source and destination IP addresses and port numbers, and the TCP sequence number. Each session based on its unique hash value is routed to a single target for the duration of the session. UDP traffic also sets up connections based on hashes, but since UDP does not contain sequence numbers, it uses source and destination IP addresses and port numbers.
The load balancer will create a new network interface in every availability zone it is configured to operate in and receives a static IP address. If the load balancer is Internet-facing, one Classic IP for each subnet can be associated with its listener interface.
Health checks are configured to monitor the targets, so connections are forwarded only to healthy endpoints.
The ELB is integrated with other AWS services such as AWS Certificate Manager, ECS container services, autoscaling, CloudTrail, Elastic Beanstalk, CloudWatch, CodeDeploy, and CloudFormation.
SSL/TLS client session termination acts as an SSL offload for the backend targets. SSL/TLS security policies are predefined and offer a large selection to meet your specific security requirements and allow for older browser support. Amazon Certificate Manager and IAM are options you can use to manage your digital certificates.
As with the ALB, SNI and sticky session features are included. Source IP addressing is preserved and passed to the target servers. You can use static IP addressing, which makes security configurations and whitelisting/blacklisting security configurations easier.
Integration with the AWS Route 53 DNS service allows DNS to remove a load balancer from the network resources should it become unavailable. By using DNS for failover, you can use Route 53 to direct traffic to active sites.
NLB pricing is based on the hours (or partial hour) that the load balancer is operational and the number of network load balancer capacity units used per hour.