In addition to AWS managed services, a large number of partner solutions are available in the AWS Marketplace. You can deploy a third-party firewall solution on a load-balanced auto scaling group of EC2 instances for a higher level of protection. This also allows you to have consistent solutions on-premises and in the cloud.
The AWS Network Firewall can provide stateless or stateful firewall rules; intrusion prevention; and filtering of URLs, IP addresses, and domains. It can secure traffic at layers 3–7.
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which options can be used to monitor logs from the AWS Network Firewall? (Choose two.)
A. Logs can be stored in a DynamoDB table and queried.
B. Logs can be stored in an S3 bucket.
C. Kinesis Firehose can be used to port logs to a third-party provider.
D. Redshift can be used to port logs to a third-party provider.
2. What types of traffic can be inspected by the AWS Network Firewall? (Choose two.)
A. HTTPS (SNI)/HTTP protocol URL filtering
B. Deep packet inspection for encrypted traffic
C. DDoS mitigation
D. Domain, port, protocol, IP addresses, and pattern matching
1. Answer: B and C are correct. AWS Network Firewall activity can be logged to an Amazon S3 bucket or to Amazon Kinesis Firehose.
2. Answer: A and D are correct. The AWS Network Firewall supports outbound traffic control using HTTPS (SNI)/HTTP protocol URL filtering, access control lists (ACLs), DNS queries, and protocol detection. AWS Network Firewall rules can be based on domain, port, protocol, IP addresses, and pattern matching.
This section covers the following objective of Domain 5 (Networking and Content Delivery) from the official AWS Certified SysOps Administrator – Associate (SOA-C02) exam guide:
5.1 Implement networking features and connectivity
If you can correctly answer these questions before going through this section, save time by skimming the Exam Alerts in this section and then completing the Cram Quiz at the end of the section.
1. What is the difference between a gateway endpoint and an interface endpoint?
2. Is an Internet gateway required when using a VPC endpoint?
1. Answer: Interface endpoints connect to a vast array of AWS services powered by PrivateLink. Gateway endpoints connect to S3 or DynamoDB.
2. Answer: No, the private Amazon backbone network is used.
A VPC endpoint is a virtual interface that allows resources inside a VPC to communicate with other AWS resources outside the VPC without traversing the Internet. For example, you can connect to an S3 bucket over the AWS private backbone using a VPC endpoint.
Interface endpoints connect to services powered by PrivateLink. This is compatible with a vast list of AWS resources, including CloudTrail, Elastic Load Balancing, Kinesis, Lambda, S3, DynamoDB, and much more. The interface endpoint is an ENI within an AWS VPC that has a private IP address within the VPC subnet of the resources that are consuming the service. This feeds traffic into a solution hosted in the service provider account. For example, a service provider has a data analysis tool running on EC2 instances in an AWS account. The service consumer can connect to those resources using an interface endpoint that is reachable inside a subnet in their own VPC. Figure 11.10 shows an interface endpoint being used by a service provider.
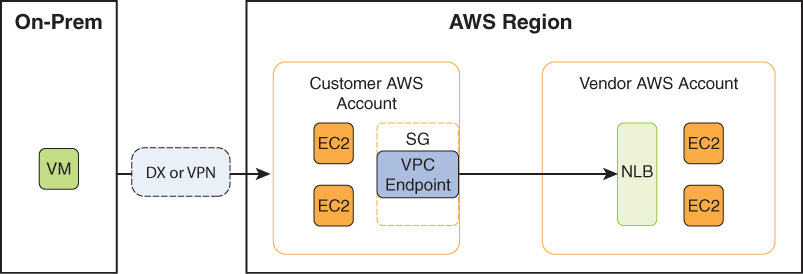
FIGURE 11.10 PrivateLink