The following quickly highlights a common response approach to an infrastructure-related security incident involving an EC2 instance:
You will not be expected to know the commands to carry out the preceding steps via the AWS CLI, but should you wish to do this, please review the steps provided in the AWS Security Incident Response Guide located in the resource section of this chapter.
Using this set of steps as a guideline, you can map out steps and create runbooks to help you and your team members respond to incidents methodically. You will see these steps in action a bit later in this chapter.
With an understanding of the steps needed to take part in the operations side of IR, now examine some of the tools that AWS offers to aid in responding to incidents.
Across the many different AWS services, there are a handful of tools you should concentrate on when it comes to IR. Some of them come in the detection phase so that you can be alerted that an incident is either in the process of occurring or has recently occurred. The other tools fall into the response or operation phase, where you take actions to mitigate the incident and return to a normal running state.
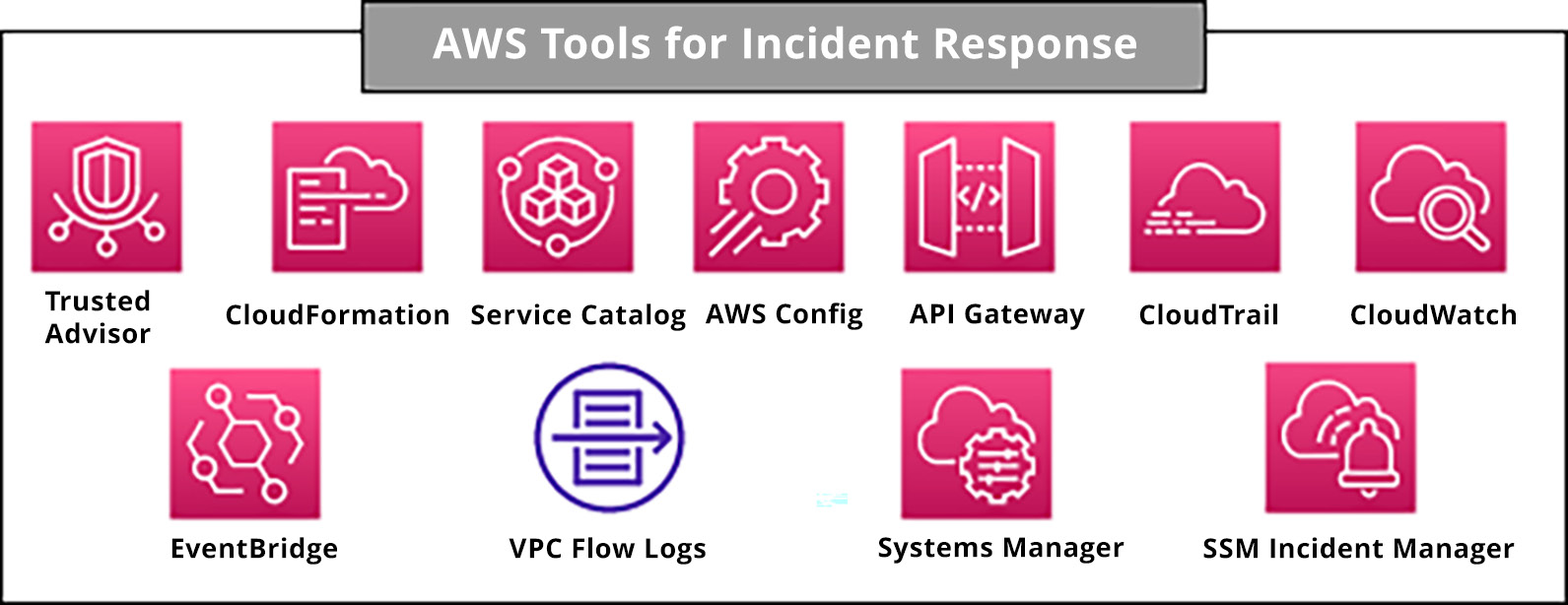
Figure 4.3: AWS Tools for IR
Having had a look at the majority of the native tools that would be used in IR, you can move on to the detection process next.
Detection can come in several different forms. There are a variety of different steps you can take: obtaining the logs for the data, visibility into your environments, and then parsing that data for relevant information to send an alert if something is out of the ordinary.
These processes are distinct but they often work together. The collected logs are shown on the services that provide visibility to you as the security or system administrator. These logs also contain the events and metrics, which trigger the alerting so that action can be taken on the account.